Fortify Your Digital Fortress with Aarohi Infotech
Providing You With best Security Services
Welcome to Aarohi Infotech, where safeguarding your digital assets is our top priority. As a leading provider of cybersecurity services, we specialize in fortifying your business against the ever-evolving landscape of online threats. With a team of seasoned experts at the helm, we offer comprehensive solutions tailored to your unique needs, ensuring peace of mind in an increasingly interconnected world. From proactive risk assessments to swift incident response, we stand by our commitment to protecting your data, reputation, and bottom line. Partner with us and embark on a journey towards fortified cyber resilience."
Here are some key aspects of managing cybersecurity:
Managing cybersecurity involves implementing measures to protect computer systems, networks, and data from unauthorized access, attacks, and breaches.
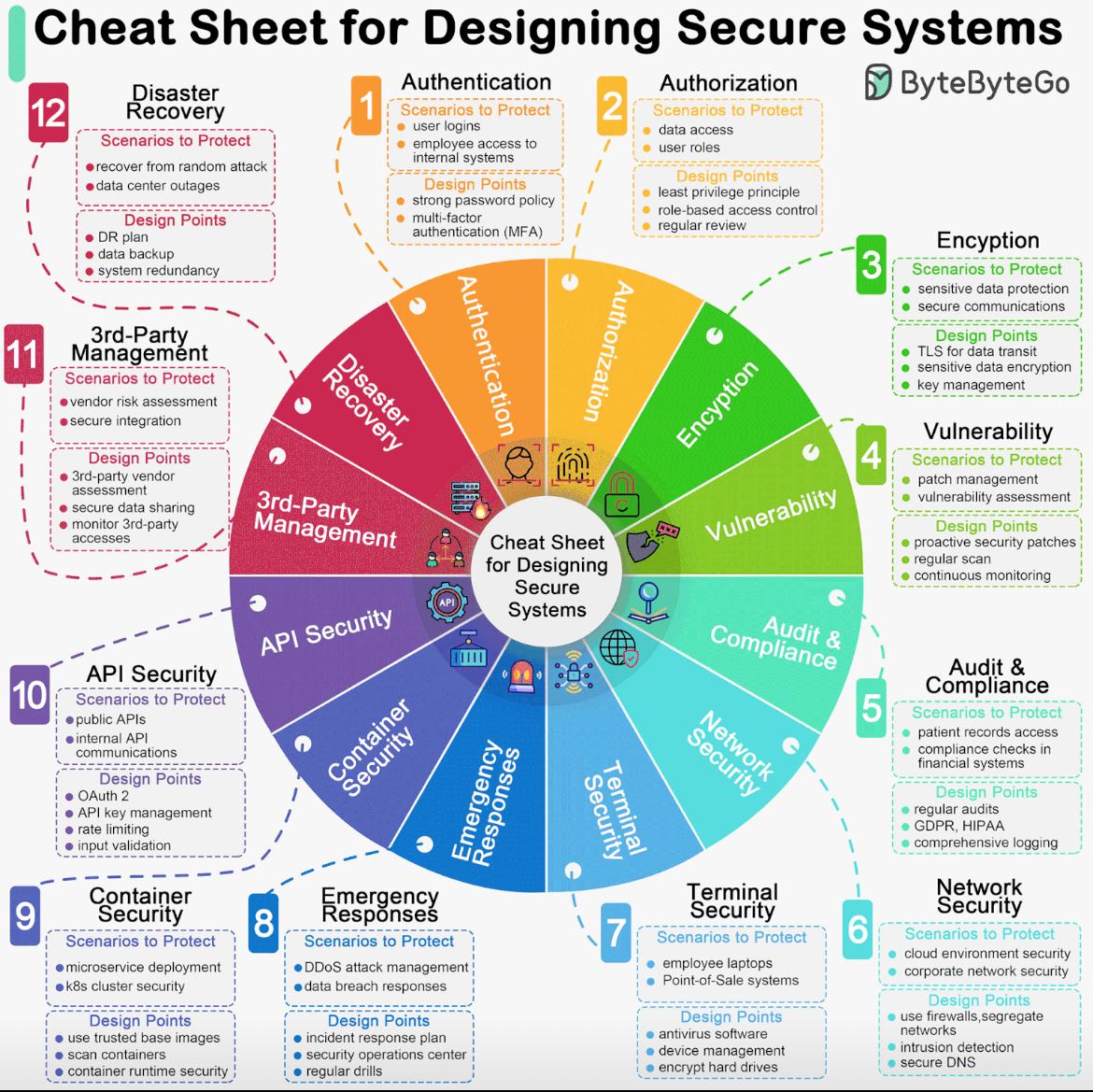
Security Policies and Procedures
Develop and enforce security policies and procedures that govern how employees, contractors, and third parties should handle sensitive information, access systems, and use technology resources. This includes policies for password management, data handling, software usage, and remote access.
Access Control
Implement access control mechanisms to restrict access to sensitive data and systems only to authorized individuals. This may involve using role-based access control (RBAC), multi-factor authentication (MFA), and least privilege principles to limit access rights based on user roles and responsibilities.
Security Awareness Training
Provide regular security awareness training to employees to educate them about common cybersecurity threats, phishing attacks, social engineering tactics, and best practices for maintaining security. Ensure that employees understand their role in maintaining cybersecurity and how to report security incidents.
Incident Response Plan
Develop and regularly update an incident response plan that outlines the steps to be taken in the event of a cybersecurity incident or breach. Define roles and responsibilities for incident response team members, establish communication channels, and conduct regular tabletop exercises to test the effectiveness of the plan.
Security Monitoring and Logging
Implement security monitoring tools and systems to continuously monitor for suspicious activities, anomalies, and potential security incidents. Collect and analyze logs from various sources, such as firewalls, intrusion detection systems (IDS), and endpoint security solutions, to detect and respond to threats in real-time.
Third-Party Risk Management
Assess and manage the cybersecurity risks associated with third-party vendors, suppliers, and service providers that have access to your organization's systems or data. Ensure that third parties adhere to your organization's security standards and contractual obligations regarding data protection.
Risk Assessment
Identify and assess potential cybersecurity risks to your organization's assets, including data, systems, and networks. Understand the potential impact of these risks on the business and prioritize them based on their severity and likelihood.
Data Protection
Implement encryption, data masking, and other data protection measures to safeguard sensitive information both at rest and in transit. Implement data loss prevention (DLP) solutions to prevent unauthorized access or leakage of sensitive data.
Vulnerability Management
Regularly scan systems and networks for vulnerabilities and weaknesses that could be exploited by attackers. Develop a process for prioritizing and remediating vulnerabilities based on their severity and potential impact on the organization's security posture.
By focusing on these key areas and adopting a proactive approach to cybersecurity management, organizations can better protect themselves against cyber threats and minimize the risk of security breaches.