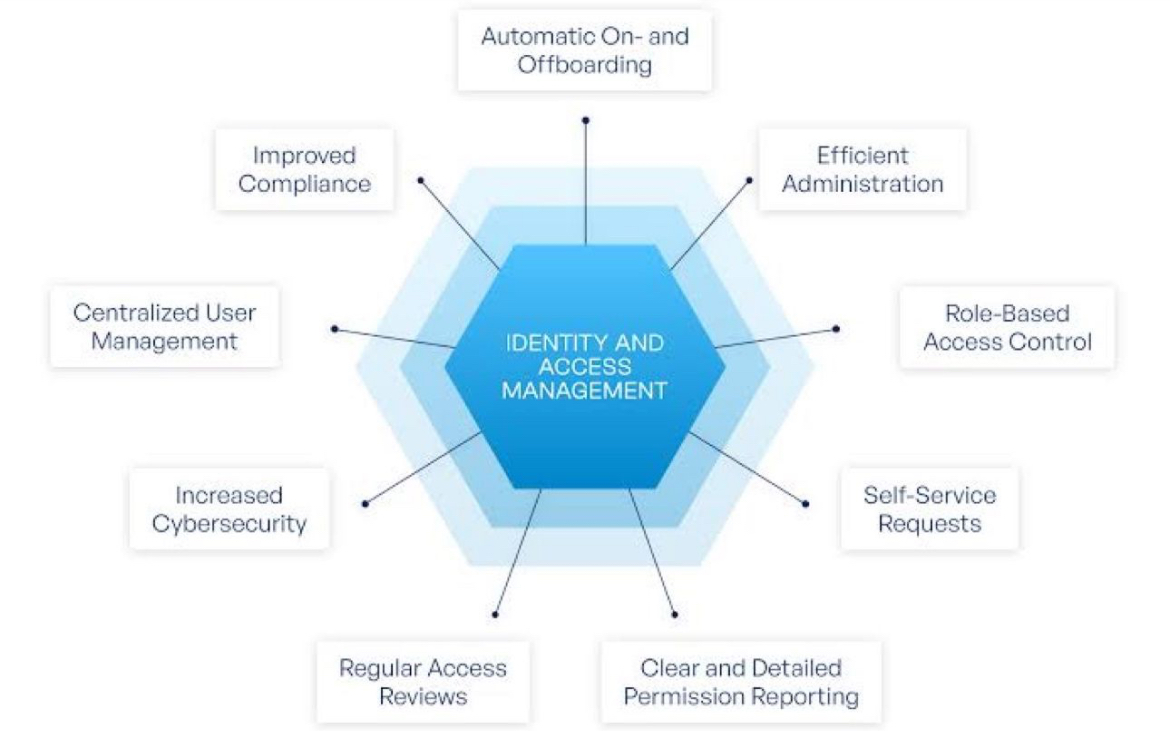
Identity Management
IAM enables organizations to manage access to your valuable assets, applications, and infrastructure. We will enable your ability to accurately provision and de-provision identities, authenticate them, and authorize their role-based access to resources and actions.
Aarohi’s specialized cross-functional project teams focus on your identity management objectives and are the keystone to your success. We employ experienced industry-recognized experts in the field of Identity and Access Management, Privileged Access Management, SAP Security, and general Application Security. Our certified consultants have many years of direct industry experience working on the latest solutions the industry has to offer and are proficient in a variety of working environments.
We accomplish your identity management needs using a variety of tools including: CA Siteminder, PingIdentity, Okta, BeyondTrust, SailPoint IdentityIQ, Saviynt, Oracle Identity Manager, OneIdentity, Microsoft Identity Manager, ForgeRock, SAP IDM, and others.

The Services we provide under IAM are:
Strategy & Roadmap development
Solution Selections and RFPs
Solution Design and Implementation
Solution optimization and revamps
Solution governance, maintenance and support
Conducting Workshops and Status Assessment
Privileged Access Management (PAM) Service
Privileged Access Management (PAM) is a subset of Identity Access Management (IAM) that assures the integrity of your infrastructure, applications, and data by controlling access to only an authorized subset of your employees.
Our PAM implementation ensures that only the users who need it (and only when they need it) have access to your organization’s most sensitive networks, systems, applications, and data. We design PAM services and solutions to keep your organization safe from the risk of compliance violations, privacy breaches, and fraud, and to eliminate the threat of compromised applications and data.
As work styles evolve, your employees access your systems from a variety of locations including corporate offices, home offices, customer locations, and airport or hotel lobbies among many others. In addition, they are using a wide range of corporate issued and personal devices. Our PAM services are designed to keep your applications and data safe in this complex and ever-changing security environment.
We apply decades of experience to help you customize an implementation to your architectural requirements, integrate a holistic methodology into your operations, and develop a framework for ongoing security and protection.
The Services we provide under PAM are: